Search Our Database
Disable DNS Recursion In Linux
Introduction
DNS recursion can be exploited in DNS amplification attacks, making it crucial for server administrators to disable this feature if it’s not needed. This guide will walk you through the steps to disable DNS recursion on a Linux server.
Steps to Disable DNS Recursion
Step 1 – Access the BIND Configuration:
- Open the main configuration file for BIND, named
named.conf
, located in
/etc/bind/or
/etc/named/
vim /etc/bind/named.conf
OR
vim /etc/named.conf
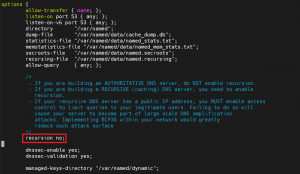
Step 2 – Edit the Configuration:
- In the
named.conf
or the appropriate configuration file, you add below details at the Options section
recursion no;
Step 3 – Restart BIND or Restart the device:
- Apply the changes by restarting the BIND service or reboot the server:
Step 4 – Test the Configuration:
- Ensure that BIND is running correctly after the changes:
sudo systemctl status bind9
- You can also test DNS functionality to ensure that the server is responding as expected.
Conclusion
Disabling DNS recursion on your Linux server is a crucial step in securing your DNS infrastructure. It helps prevent your server from being exploited in DNS amplification attacks and reduces the risk of being used as a part of a distributed denial-of-service (DDoS) attack. After completing these steps, your server should no longer respond to recursive query requests from unauthorized clients.
Remember, always back up configuration files before making changes, and carefully test your DNS server after applying new settings to ensure that it functions as expected.
Should you have any inquiries of the guidelines, please feel free to open a ticket through your portal account or contact us at +603 – 2026 1688. We’ll be happy to assist you further