Search Our Database
How to restrict RDP Access to specific IP Addresses on Windows Server
Introduction
Remote Desktop Protocol (RDP) enables remote access to Windows servers, making it crucial to restrict access to specific IP addresses for security purposes. By limiting RDP access to trusted IPs, administrators can reduce unauthorized access risks and safeguard critical server data. This guide explains how to restrict RDP access to specific IP addresses on a Windows Server using Windows Firewall with Advanced Security, providing a practical approach for administrators to enhance security by allowing only authorized IP addresses to establish RDP connections.
Prerequisites
- Administrative access to the Windows Server
- A list of IP addresses that you wish to allow RDP access
- Backup of your current firewall settings
Step-by-Step Guide
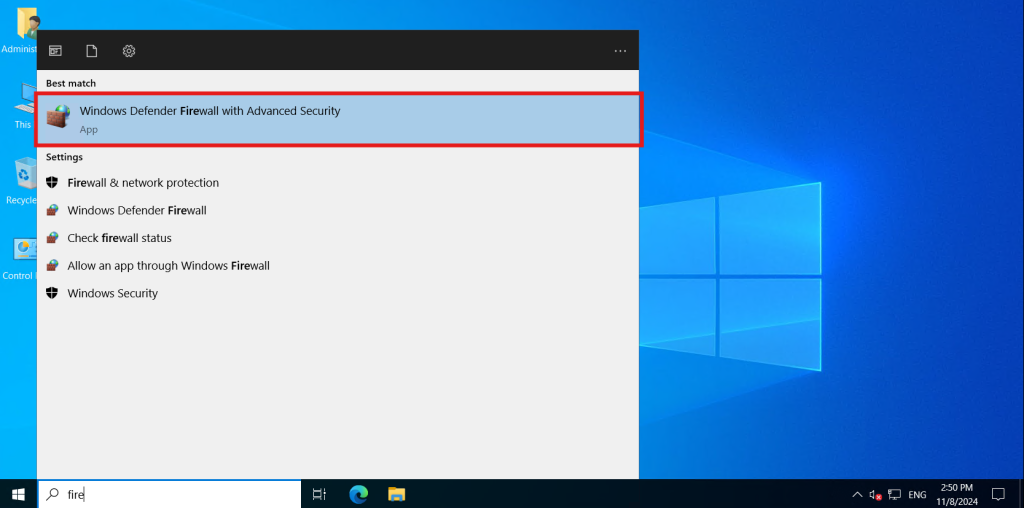
Step 1: Open Windows Firewall with Advanced Security
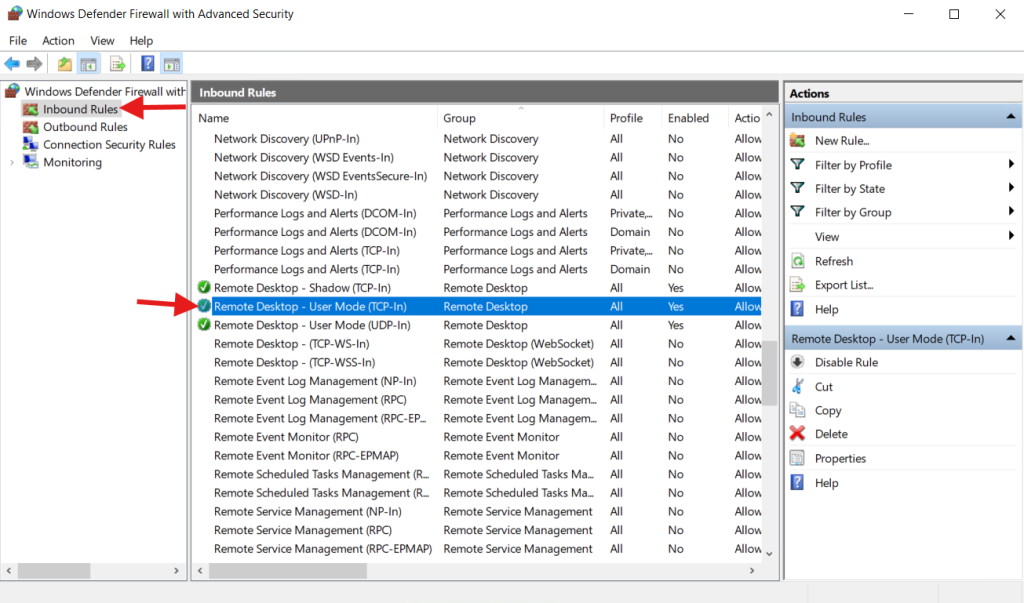
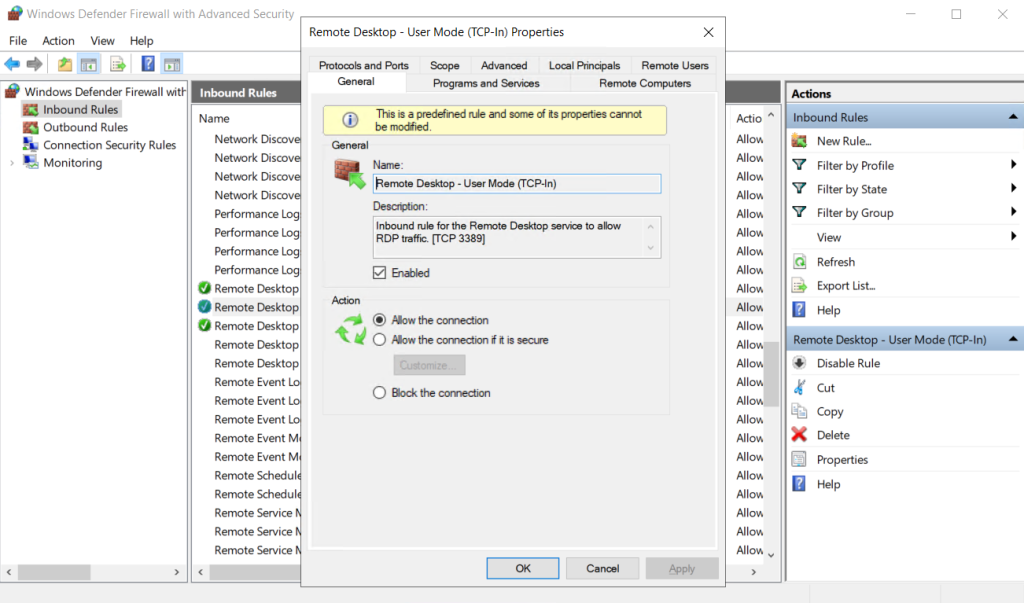
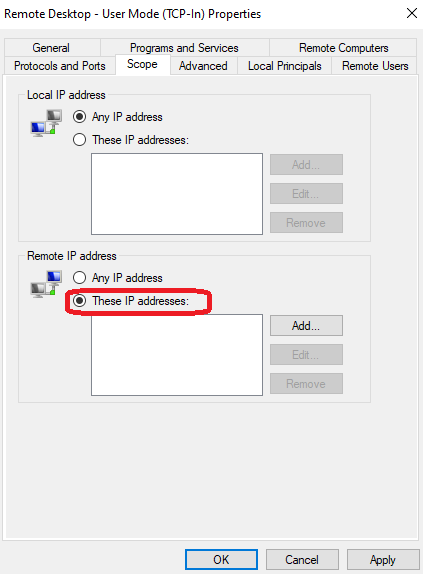
Step 2: Edit the RDP Inbound Rule details
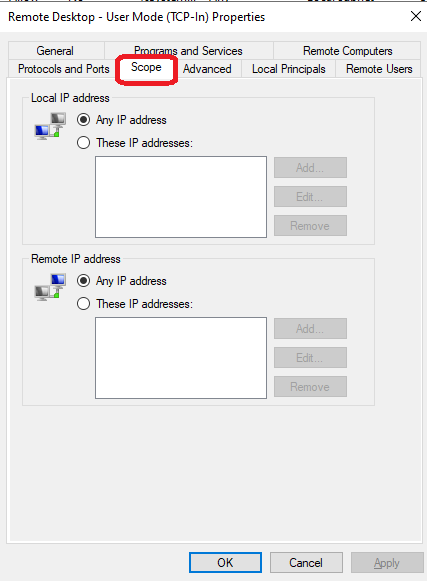
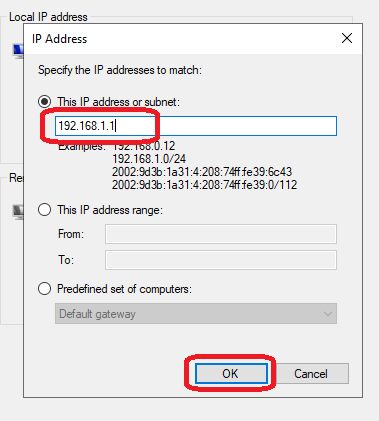
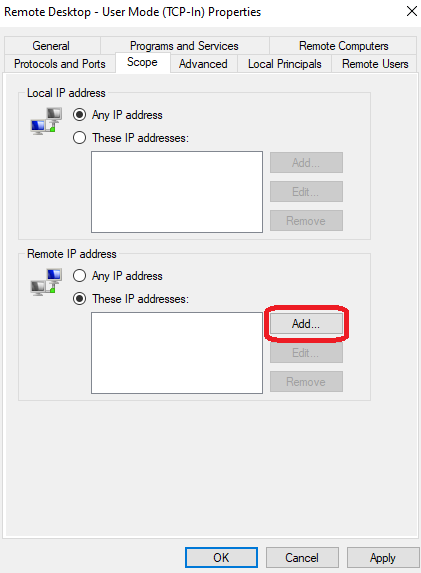
- Click Add and enter the IP addresses that you wish to allow RDP access. You can add multiple IPs or a range.
Conclusion
You have now successfully configured your Windows Server to only allow RDP connections from specific IP addresses. This setup enhances your server’s security by ensuring only authorized users can establish remote desktop sessions.
For additional assistance or if you encounter any issues, please contact our support team at support@ipserverone.com.
Article posted on 25 March 2024 by Tze Hing.