Search Our Database
How to Enable Password Authentication and Login as Root User in Linux Cloud Server
Overview
By default, all Linux instances will use private key for access authentication. This tutorial will guide you through disable key authentication and use the root password to login and optionally disable the default generated key pair.
Prerequisite
- Login to your Linux instance via SSH using the default user. We will be using PuTTY as our SSH client for this tutorial.
Note
Notice that “centos” is shown here in this tutorial as the default login user and path because this instance is running on the CentOS image. The default user and path will differ based on the image of your choice.
Ubuntu Image – “ubuntu” default user
Debian Image – “debian” default user
CentOS Image – “centos” default user
AlmaLinux Image – “almalinux” default user
Rocky Linux Image – “rockylinux” default user
OpenSUSE Image – “opensuse” default user
Instructions
Step 1: Login to your Linux instance via PuTTY.
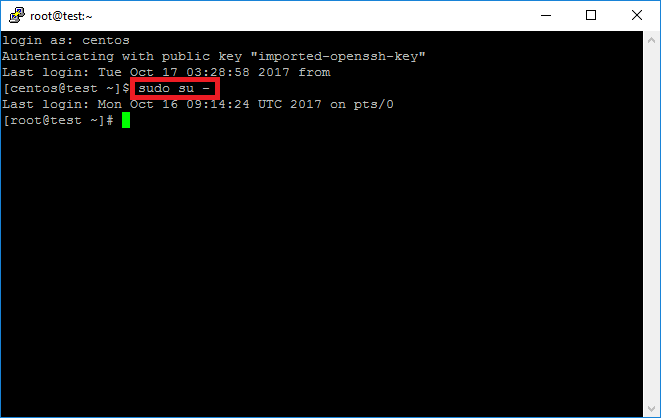
Step 2: In the terminal, enter “sudo su –” to switch to your root user in order to make changes to the system.
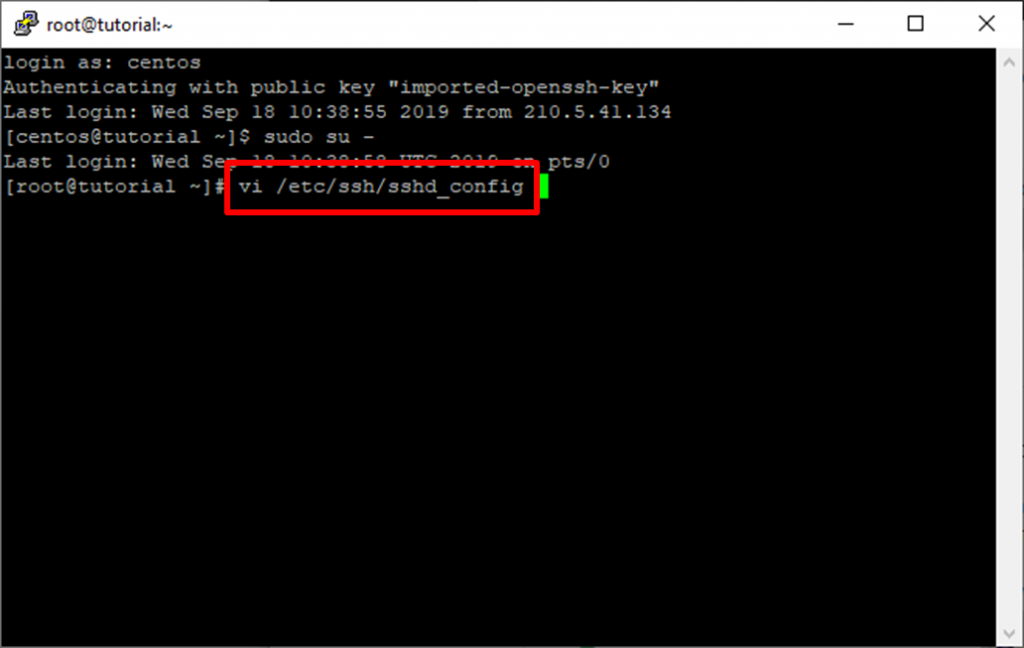
Step 3: Edit “/etc/ssh/sshd_config” with your favorite editor. We will use vi for this tutorial.
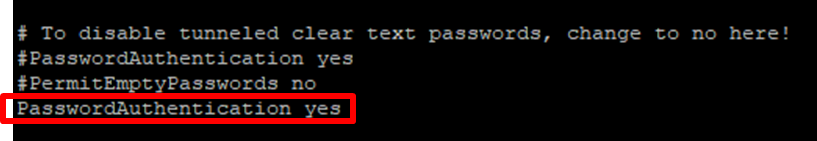
Step 4: Press “i” for insert and change the “PasswordAuthentication” to yes and press “esc” to exit from editing. Enter :wq! to save and press “enter” to confirm.
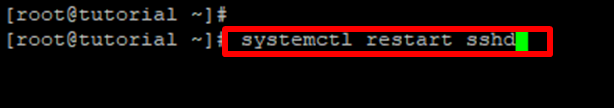
Step 5: Restart sshd with “systemctl restart sshd”.
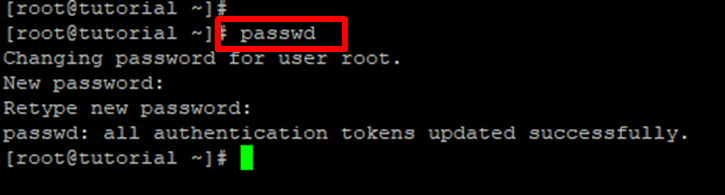
Step 6: Set a password for the root user with “passwd”, you will need to input your specified password twice.
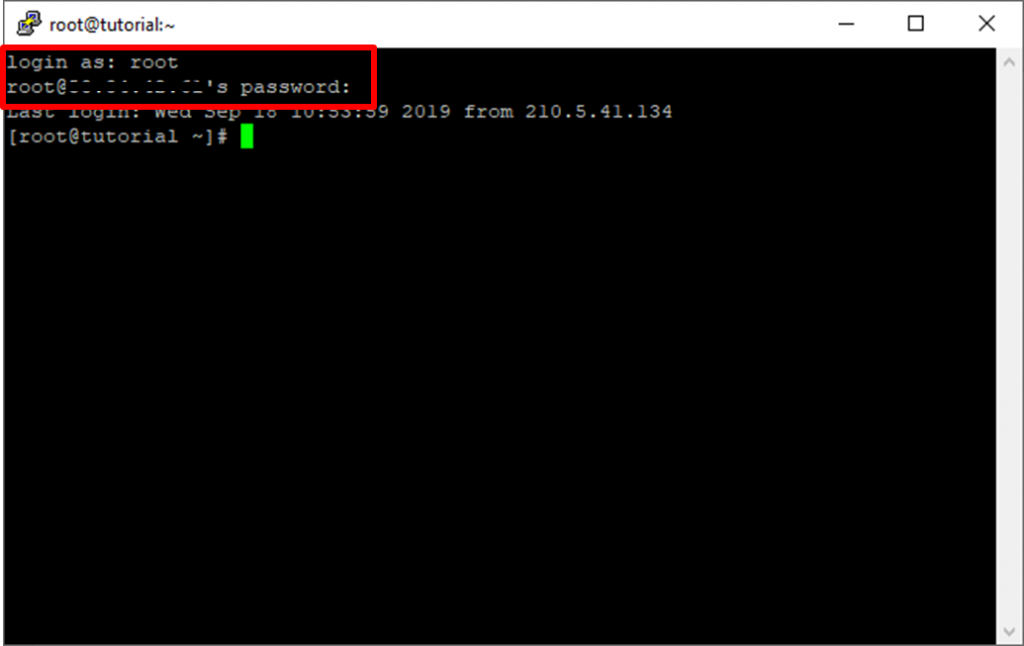
Step 7: End and exit the session. Re-login as root user without ssh key and enter the password for root.
Step 8: (Optional) Check and remove the default key pair. Edit the “authorized_keys” file with your preferred editor, we will be using the “vi” text editor. Enter “vi /home/centos/.ssh/authorized_keys” in the terminal/command line.
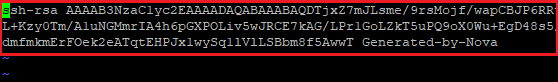
Step 9: (Optional) Delete the default public key entry (Generated-by-Nova) in the “authorized_keys” file and save the changes.
Note: You need to delete the whole line starting from ‘ssh-rsa’.
IMPORTANT: Please take note that enabling password authentication and using root user for login might impose brute-force attack towards your server. You are also advised to change the default SSH port.