Search Our Database
Enabling and Enforcing Two-Factor Authentication (2FA) in DirectAdmin (GUI)
Introduction
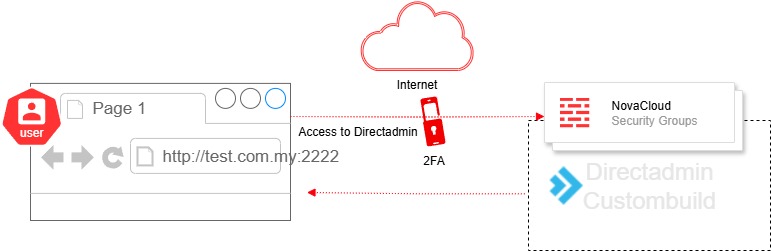
This guide explains how to enable and configure Two-Factor Authentication (2FA) in DirectAdmin (Evolution Skin) for Admin.
Enabling 2FA is a critical step in reducing account takeover risks, especially in legacy environments where users may still rely solely on username and password login. Legacy systems lacking additional authentication mechanisms are increasingly vulnerable to brute-force attacks, credential stuffing, and phishing attempts. Implementing 2FA introduces an essential second layer of defense, significantly lowering the risk of unauthorized access even when credentials are compromised.
DirectAdmin supports 2FA via Time-Based One-Time Password (TOTP), compatible with popular authentication applications such as Google Authenticator, Authy, and Microsoft Authenticator.
Prerequisites
- Console access via Customer Portal Console Access
- Admin-level access to DirectAdmin panel (GUI) or root shell (CLI)
- DirectAdmin configured with Evolution skin
- Valid DirectAdmin license
- Mobile device with a supported TOTP application (such as Google Authenticator)
- HTTPS properly configured and enabled on the server
Impact
- Login Flow Changes: Users must complete an extra authentication step (TOTP code) after entering their password.
- Access Denied Without Setup: If 2FA is enforced via directadmin.conf, users who haven’t configured 2FA will be unable to log in until they complete setup.
- User Confusion: Legacy users unfamiliar with 2FA or TOTP apps may require support to walkthrough the process in the app.
- Lockout Risk: If users lose access to their TOTP device and backup codes, they may be permanently locked out and requires admin intervention.
- Increased Support Tickets: Expect more ticket during initial rollout, especially related how to perform QR code scanning, code mismatch, or lost devices.
- Incompatibility with Older Clients: Older mobile devices or unsupported TOTP apps may fail to sync properly.
Best Practices
- Enabling 2FA through directadmin.conf provides centralized enforcement and is strongly recommended for environments handling sensitive workloads. Refer to https://docs.directadmin.com/directadmin/general-usage/securing-da-panel.html#two-step-authentication
- Legacy users will continue to use standard login unless 2FA is enforced or configured manually
- YubiKey and FIDO2 hardware keys are not natively supported in current DirectAdmin builds
- Backup codes are critical for account recovery and should be securely archived
Step-by-Step Guide
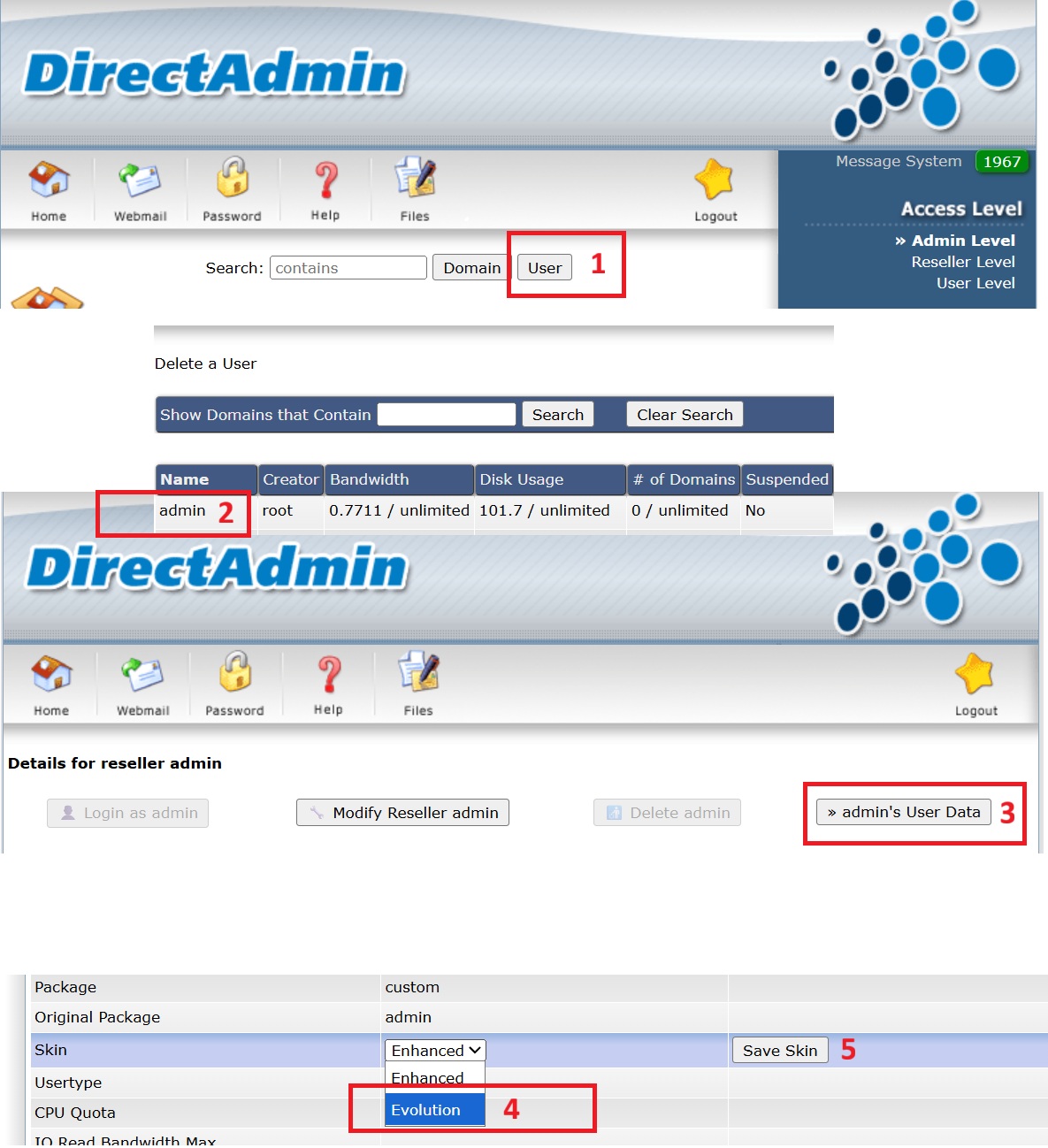
Change from Enhanced to Evolution Skin in DirectAdmin (Directadmin GUI)
- Log in to Directadmin
- Navigate to User > admin > admin’s user data > Evolution > Save
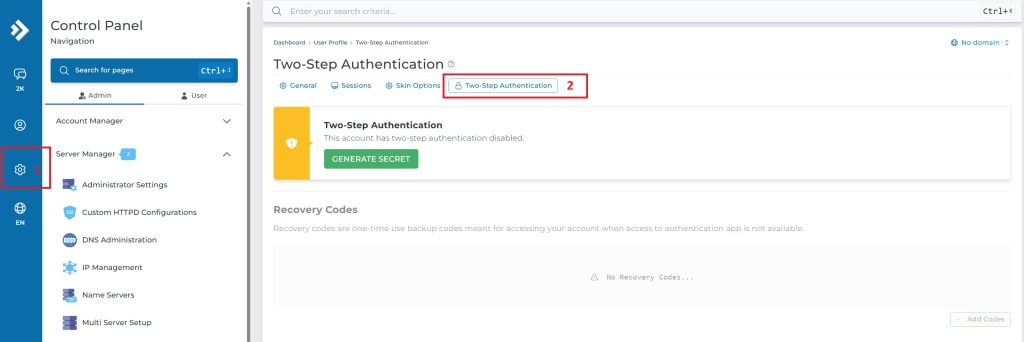
Enable Two Step Authentication 2FA (Directadmin GUI)
- Log in to Directadmin
- Navigate to Setting > Two-Step Authentication > Generate Secret
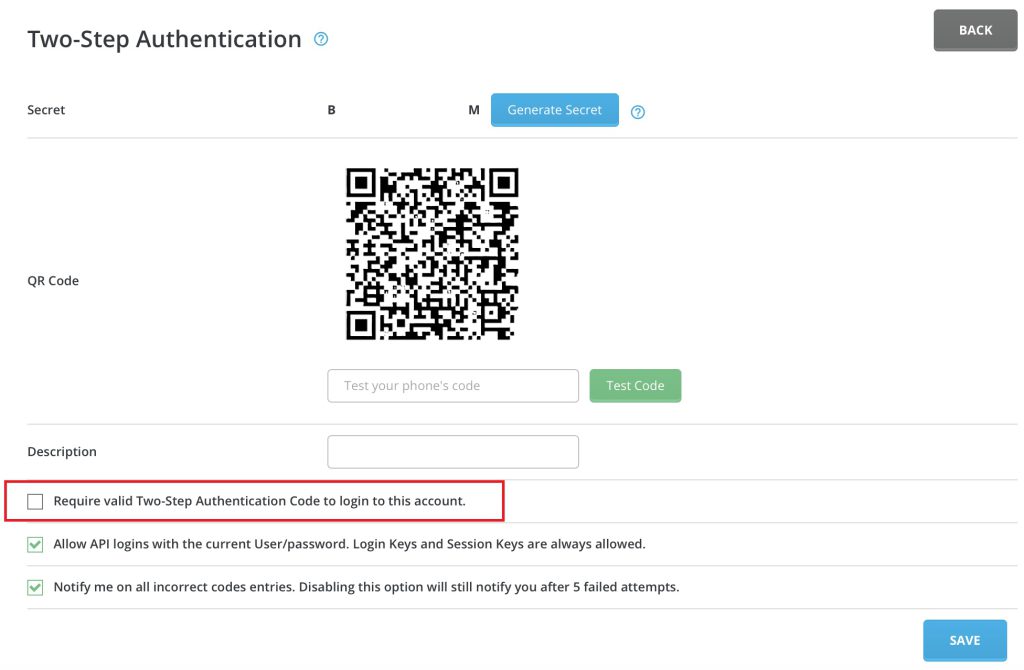
- Scan QR code with your phone (Google Authenticator) , enter the code > Test code > valid code > Save
- Logout Directadmin, Login Directadmin again, to test two-factor authentication code
For user comfortable with CLI
- refer to https://docs.directadmin.com/changelog/version-1.48.1.html#two-step-authentication-skins-lang
ssh root@your-server-ip cd /usr/local/directadmin/conf/ vi directadmin.conf max_twostep_auth_attempts=5 twostep_auth=1 twostep_auth_discrepancy=1 twostep_auth_trust_days=30
(Optional) Directadmin blacklist / whitelist
- To prevent your admin user lockout for entering too many times incorrect OTP
- remove blocked IP in /usr/local/directadmin/data/admin/ip_blacklist
- if you have trusted IP, you may add it in /usr/local/directadmin/data/admin/ip_whitelist
References
https://docs.directadmin.com/changelog/version-1.48.1.html#two-step-authentication-skins-lang
https://docs.directadmin.com/directadmin/general-usage/securing-da-panel.html
Conclusion
Securing access to your DirectAdmin panel with Two-Factor Authentication it’s about taking real, proactive steps to protect your users and your systems. Username and Passwords alone are no longer enough, securing server must go beyond password, enabling Two-Factor Authentication (2FA) strengthens account protection by introducing a second layer of verification. By integrating 2FA into routine access controls, administrators reduce operational risk, is simple to deploy yet highly effective in mitigating unauthorized access.
“The smallest step like entering a 6-digit code … can make the big difference.”
Need Help?
Reach out to our support team at support@ipserverone.com for assistance.