Search Our Database
Securing Web Traffic using Modsecurity and Cloudflare
Introduction
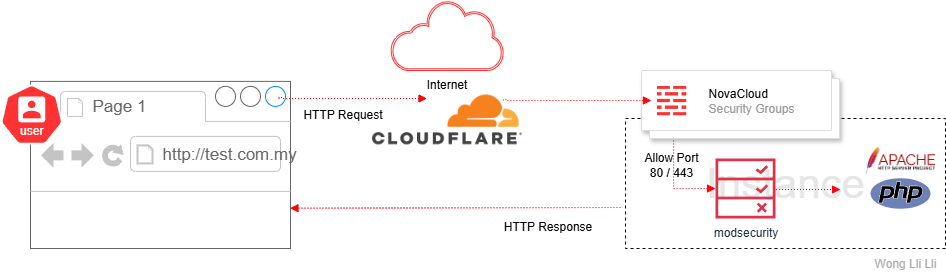
This guide explains how to secure your website in your Novacloud instance by adding Modsecurity (Layer 7 WAF) alongside Cloudflare (WAF + CDN).
Traditional Firewall operate at layer 3 / 4 (IP / Port), block traffic based on source IP, port or protocol.
Modsecurity operate at layer 7 (Application), inspects HTTP requests to detect and block malicious behavior based on application-layer patterns.
Cloudflare as a reverse proxy, place between your web server and the internet. It enhances both security and performance without requiring major changes to your web server:
- WAF at the Edge: Blocks malicious traffic before it reaches your origin server.
- DDoS Protection: Automatically mitigates volumetric and application-layer attacks.
- Bot Management: Detects and filters bad bots while allowing legitimate crawlers.
- Global CDN: Speeds up content delivery through caching across worldwide data centers.
- SSL/TLS Offloading: Encrypts traffic with minimal configuration on your server.
- DNS Control: Centralized DNS management with fast propagation and built-in failover.
Prerequisites
- Access to your hosting panel (cPanel, DirectAdmin) or root shell (CLI)
- Basic understanding of HTTP protocols
- DNS managed by Cloudflare
What is Modsecurity?
ModSecurity is an open-source Web Application Firewall (WAF) deployed at the web server layer to monitor, log, and block HTTP traffic based on predefined rules.
- Monitors HTTP/S requests and responses
- Detects and blocks malicious behavior using custom rules or community ruleset (e.g. OWASP)
- Works with Apache, NGINX (via connector), and LiteSpeed
What is Traffic Modsecurity Scan?
ModSecurity scans dynamic HTTP or HTTP/S traffic:
- .php, .asp, .jsp, .cgi (based on URL and content-type)
- GET and POST requests with query strings, form data, cookies, headers
- PUT, DELETE, PATCH methods for RESTful APIs
- AJAX and background HTTP calls (common in WordPress, Joomla, etc.)
- File uploads via multipart/form-data
- API calls with JSON/XML payloads
- WebSocket handshake headers (limited)
It scans HTTP payloads, not the file system itself.
It does NOT scan :
- Static file content (e.g., .jpg, .css, .js) beyond metadata
- Encrypted payloads without TLS termination
Recommended Rulesets
OWASP Core Rule Set (CRS) – Open source, broad coverage
Malware.Expert – Premium, optimized for performance and low false positives
Impact
- False Positives: May break AJAX or REST APIs
- Performance: Heavy rulesets can impact server performance (required fine tuning)
- Access Loss: Blocking admin requests or API calls (e.g. update WordPress as wp-admin, some changes are not saved)
Best Practices
- Always test changes on staging before live deployment
- Pair with Fail2Ban or CSF to ban abusive IP
- Cloudflare handles edge protection, ModSecurity handles origin-level threats
- Do not disable ModSecurity entirely if false positives occur, use rule ID exclusions. Whitelist legitimate false positives with SecRuleRemoveById
- Combine Cloudflare and ModSecurity for layered defense
- Review and Audit Regularly
- Pair with other security measures such as MFA, Captcha, VPNs and role-based authentication for added web server security.
Step-by-Step Guide
Enabling ModSecurity in WHM (GUI)
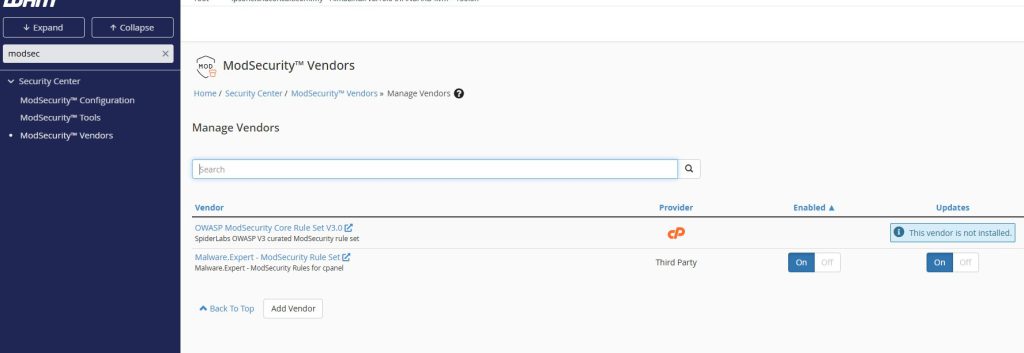
- Log in to WHM
- Navigate to Security Center > ModSecurity™ Vendors
- Click Install next to OWASP
- After installation, set configuration to On / Off.
- (Optionally) you can install third party ruleset by click on Add Vendor
- Go to Security Center > ModSecurity™ Configuration
- Set configuration to On, apply rules to specific domains or globally
Enabling ModSecurity in DirectAdmin(GUI) Evo skin
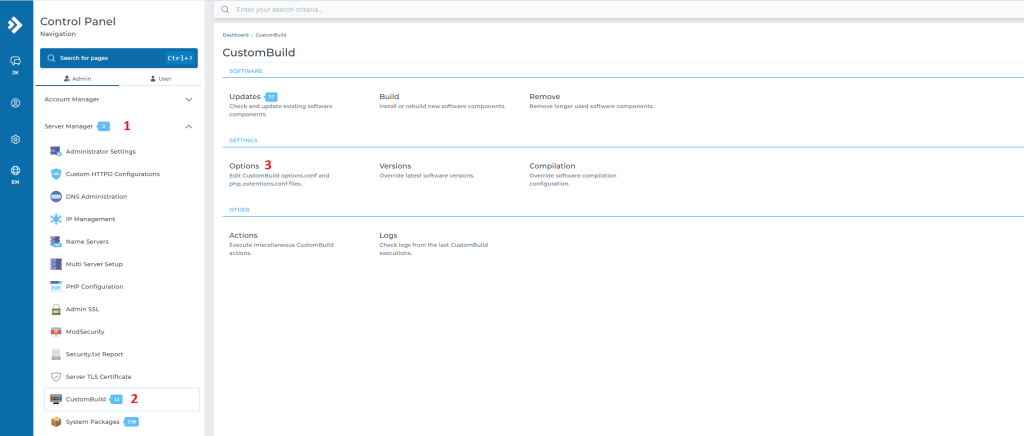
- Log in to Directadmin
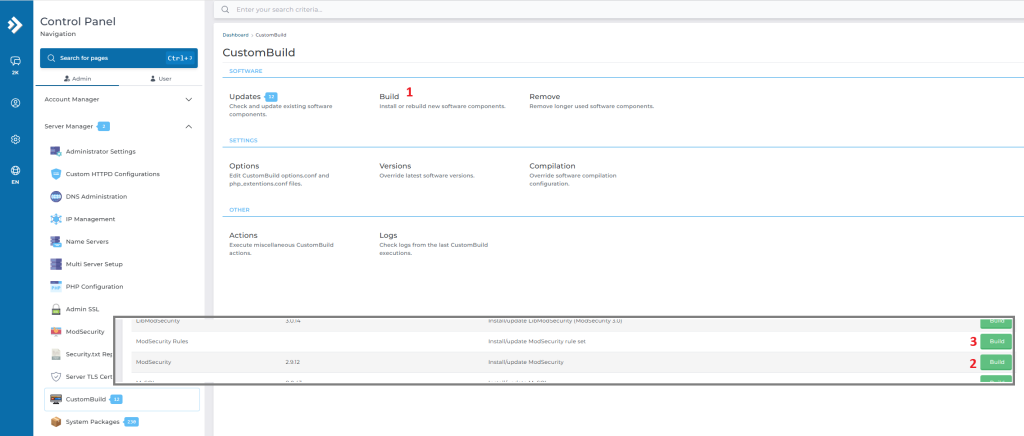
- Navigate to Server Manager > Custombuild > Options
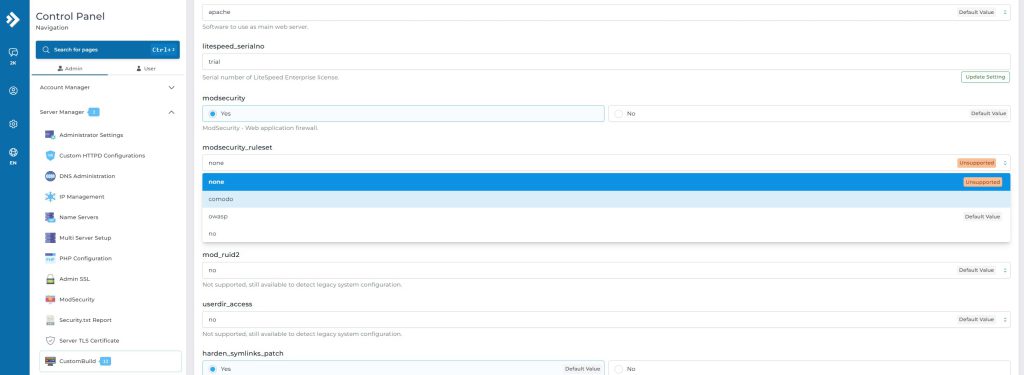
- Click radio button in modsecurity to yes
- Example, ruleset select OWASP
- Wait for 1-2 seconds (auto saved)
- Back to previous screen, click Build
For user comfortable with CLI managing Directadmin
ssh root@your-server-ip cd /usr/local/directadmin/custombuild ./build set modsecurity yes ./build set modsecurity_ruleset owasp ./build modsecurity ./build rewrite_confs ./build apache
Enabling Cloudflare for Additional Protection
Cloudflare Free and paid plans support essential security features like DNS management, SSL, and basic WAF rules. For more advanced protections (e.g., custom WAF rules, Bot Management, detailed analytics), upgrading to a Pro or higher plan is recommended, but it’s not mandatory for basic protection.
- Ensure your domain is pointed to Cloudflare DNS
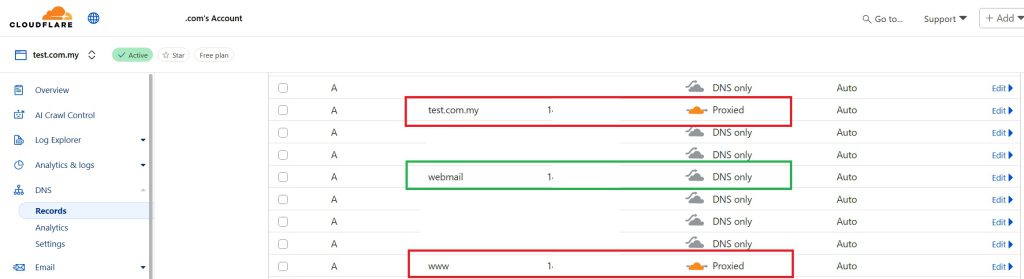
- Log in to Cloudflare Dashboard > DNS > Records
-
Cloudflare Orange Proxy (Proxied – Orange) :
Enables Cloudflare’s protection and CDN features for a domain-
Traffic passes through Cloudflare, activating WAF, DDoS protection, caching, and HTTPS.
-
Recommended for web traffic (HTTP/HTTPS).
- in this example, we enabled Cloudflare proxy (orange colour) for domain.com and www.domain.com
-
-
Cloudflare DNS Only (DNS only – grey):
Used for non-web services like email (MX, mail.domain.com, webmail.domain.com).-
Cloudflare does not proxy or filter traffic.
-
Ensures direct delivery and avoids SMTP blocking or SSL certificate issues.
-
- Go to Security > WAF to setup your WAF / custom rules. Please refer to official guide : https://developers.cloudflare.com/waf/managed-rules/deploy-zone-dashboard .
- Enable the following:
- Managed Rulesets
- Bot Fight Mode
- Super Bot Protection (Enterprise only)
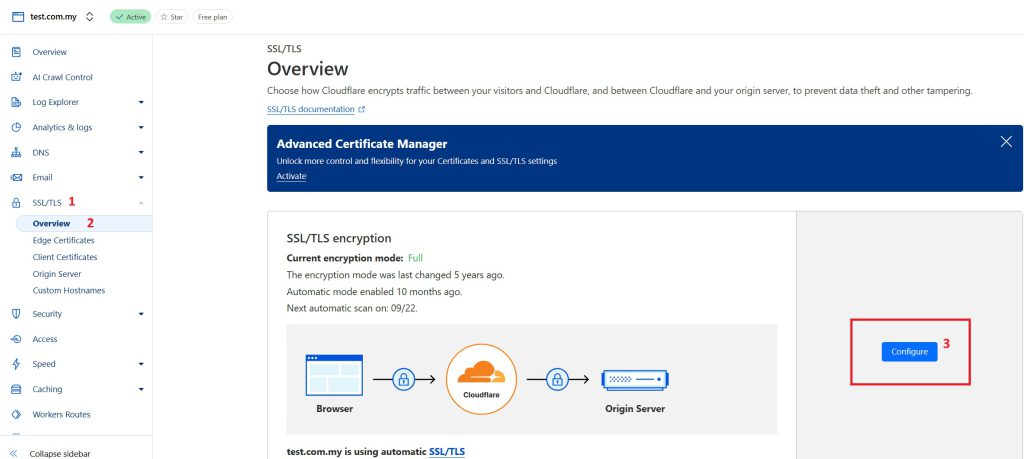
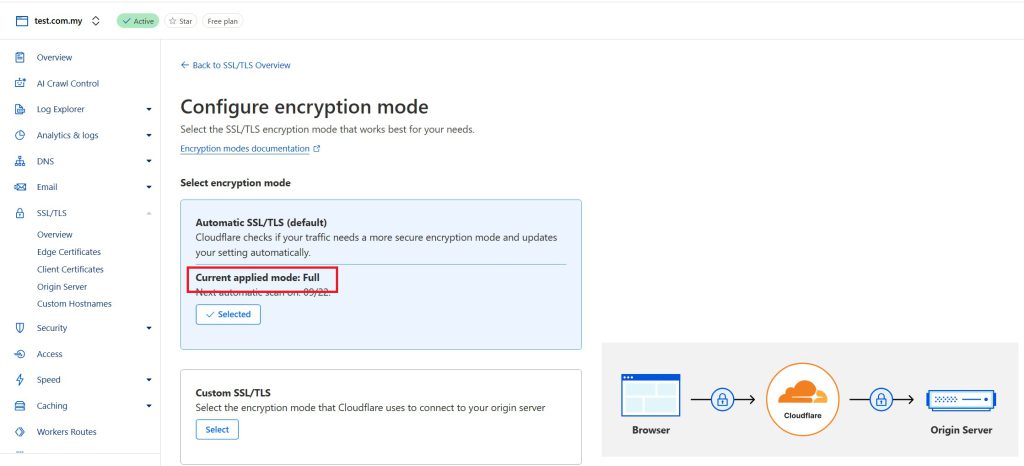
- Ensure SSL mode is set to Full (strict)
- Test your application functionality to avoid false blocks
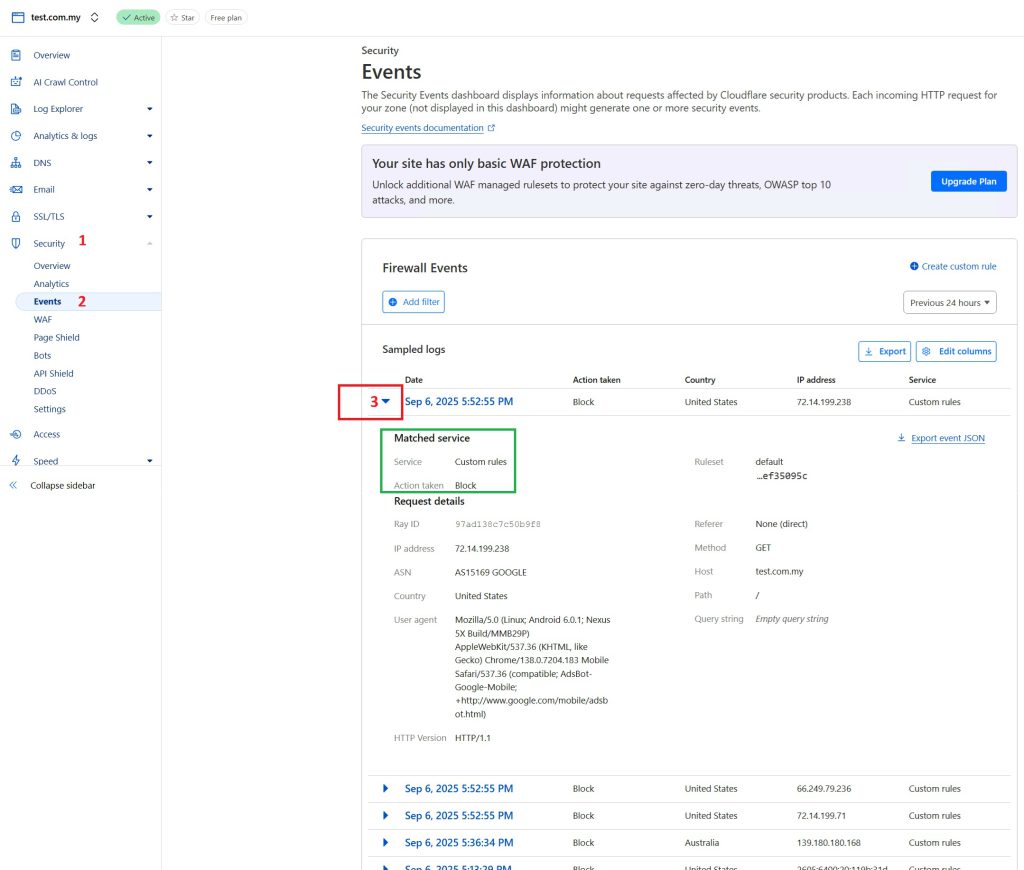
- You can review the blockages in Security > Security Events https://developers.cloudflare.com/waf/analytics/security-events/
- (optional) Click on Add Filter if you are searching for specific URL or IP
References
https://coreruleset.org/
https://github.com/SpiderLabs/ModSecurity
https://docs.cpanel.net/whm/security-center/modsecurity-tools/
https://docs.directadmin.com/webservices/apache/modsecurity.html
https://developers.cloudflare.com/waf/managed-rulesets/
Conclusion
ModSecurity with Cloudflare isn’t just a technical upgrade, it’s a strategic defense approach. ModSecurity scan deep into HTTP traffic, blocking malicious intent before it reaches your application, while Cloudflare stands as first line of defense at the edge, blocking threats at scale. When these tools are configured properly and maintained, you’re not just reacting to threats, you’re actively reducing attack surface of your web application to common web threats against unauthorized access while maintaining operational control.
Always remember: security is not a one-time setup, but an ongoing process of staying ahead, monitoring, tuning, and adapting.
“Security is when done right, letting you focus on growth, not threats.”
Need Help?
Reach out to our support team at support@ipserverone.com for assistance.