Search Our Database
Securing phpMyAdmin in DirectAdmin
Introduction
This guide explains how to properly secure Directadmin phpMyAdmin in your Novacloud instance, covering access control, authentication, IP restrictions, and integration with DirectAdmin’s SSO session.
In a standard DirectAdmin environment, phpMyAdmin is accessible via https://domain.com/phpmyadmin or https://domain.com/pma. While this makes database management easy for users, it also poses a major security risk if left unprotected.
Prerequisites
- Access to your hosting panel DirectAdmin GUI or via root shell (CLI)
- phpMyAdmin already installed via CustomBuild
- Familiarity with editing .htaccess, Apache config, or DirectAdmin’s CustomBuild system
- With proper server hostname, server hostname able to resolve in DNS
- Basic understanding of HTTP protocols
What is phpMyAdmin?
phpMyAdmin is a web-based database management tool that lets users interact with MySQL or MariaDB using a browser.
It’s widely adopted in shared hosting and control panel environments because it allows users to:
- View and edit database tables
- Import/export databases
- Run SQL queries
- Manage database users
Why It’s a Security Risk in Basic Setups?
- Exposed by Default: Often available publicly at /phpmyadmin, making it easily discoverable.
- No Access Control: Accessible to the internet without IP filtering.
- Weak Credentials: May rely solely on database user login, increasing brute-force risk.
- Outdated Versions: Some setups use older versions, exposing known vulnerabilities.
- No HTTPS Enforcement: Allows interception of credentials if SSL is not enforced.
phpMyAdmin is publicly accessible, it should be regular updates to patch vulnerabilities as it risks :
- SQL injection
- Cross-site scripting (XSS)
- Authentication bypass
- Remote code execution
Failure to keep it secure and updated can result in full database compromise, data leaks, or privilege escalation.
Potential Impact when perform hardening on phpMyAdmin login page
- User Access Changes: If SSO or IP restrictions are enforced, users must log in via DirectAdmin, which may require Directadmin access training.
- 2FA should be enforced: Directadmin login with 2FA is essential because phpmyadmin can be login with SSO button (does not required username and password) https://www.ipserverone.info/knowledge-base/how-to-launch-phpmyadmin-on-directadmin-enhanced-skin/
- Backup: Before disabling or modifying access paths, ensure you have database and config backups.
- Access from DirectAdmin only: direct links/bookmarks to /phpmyadmin will no longer work.
- Ideal for hardened or internal-use systems, but may be inconvenient for third-party or external vendor.
Requires clear internal communication and potentially affects.
Step-by-Step Guide
Option 1 : add .htaccess and IP restrictions
Create .htaccess, only allow from trusted IP in this file /var/www/html/phpMyAdmin/.htaccess
<Limit GET POST>
order deny,allow
deny from all
allow from 111.111.111.111
allow from 222.222.222.222
</Limit>
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
To ensure your security setting persists in PhpMyAdmin, consider to put the .htaccess in custom location to maintain those customizations between updates by CustomBuild :
/usr/local/directadmin/custombuild/custom/phpmyadmin/.htaccess
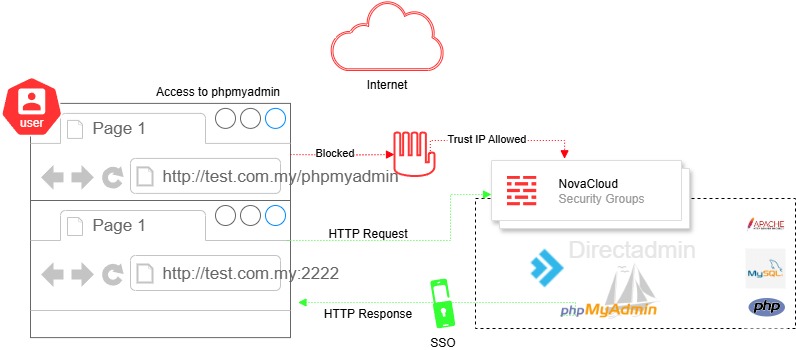
If you’re using the trusted IP example 111.111.111.111 to login from your browser https://domain.com/phpmyadmin , the page will load :
If you’re accessing from public let say 111.111.111.112 to login from browser https://domain.com/phpmyadmin , the page will not load :
Option 2 : Disable phpmyadmin public access, only allow from Directadmin SSO
Enable phpMyAdmin SSO feature
SSH to the servercd /usr/local/directadmin/
./directadmin set one_click_pma_login 1 restart
phpMyAdmin SSO-only accessible
cd /usr/local/directadmin/custombuild
./build set_fastest
./build update
./build set phpmyadmin_public no
./build phpmyadmin
Apply Configurations
cd /usr/local/directadmin/custombuild
./build rewrite_confs
systemctl restart httpd
Option 3 : Uninstall phpMyAdmin Entirely
chmod 000 /var/www/html/phpmyadmin
or Uninstall phpMyAdmin Entirely (If Never Used)
Verification
- Try HTTP URL, should redirect to HTTPS
- https://domain.com/phpmyadmin should return 404 not found or access denied
- Access via DirectAdmin panel – launches phpMyAdmin without needing a separate login (SSO works)
- IPs not whitelisted in .htaccess should be denied 403 Forbidden
Note
You might have think of creative way, such as removing the default Apache alias (/phpmyadmin) and replacing it with something less obvious let say /abc
There’s a file that keep HTTP alias for Directadmin, in /etc/httpd/conf/extra/httpd-alias.conf . Assume you remove all related entries and to add Alias /abc /var/www/html/phpMyAdmin
This change allows users to access phpMyAdmin via: https://domain.com/abc
Alias /.well-known/acme-challenge /var/www/html/.well-known/acme-challenge Alias /config /var/www/html/redirect.php Alias /roundcube /var/www/html/roundcube Alias /webmail /var/www/html/roundcube Alias /phpMyAdmin /var/www/html/phpMyAdmin Alias /phpmyadmin /var/www/html/phpMyAdmin Alias /pma /var/www/html/phpMyAdmin
This does not secure phpMyAdmin, obscuring the path only hides the location but it doesn’t prevent access. Attackers use automated tools to scan thousands of path variations, once discovered phpMyAdmin is fully exposed.
“Using a custom alias like /abc offers minimal protection and requires compensated controls.”
References
https://docs.directadmin.com/other-hosting-services/mariadb-mysql/phpmyadmin.html
https://www.phpmyadmin.net/docs/
https://forum.directadmin.com/threads/phpmyadmin-public-not-working.67860/
Conclusion
phpMyAdmin is a powerful tool for easy database management, but its default public exposure poses a significant security risk. Simply renaming or obscuring its URL is not enough. To ensure secure access, it’s essential to implement proper authentication, restrict access by IP, enforce HTTPS, and use DirectAdmin’s SSO with 2FA where possible. It must be hardened like any administrative access, secure it accordingly.
Need Help?
Reach out to our support team at support@ipserverone.com for assistance.