Search Our Database
How to Check the Log of Failed RDP Login Attempts from a Windows Server
Introduction
Monitoring failed RDP login attempts is crucial for maintaining server security and identifying unauthorized access attempts. Windows Server keeps detailed logs of these events, which you can review using the built-in Event Viewer tool. This guide walks you through locating and interpreting these logs.
Prerequisites
- Administrator access to the Windows Server
- Auditing enabled for logon events (enabled by default)
- Access to the Event Viewer utility
Step-by-Step Guide
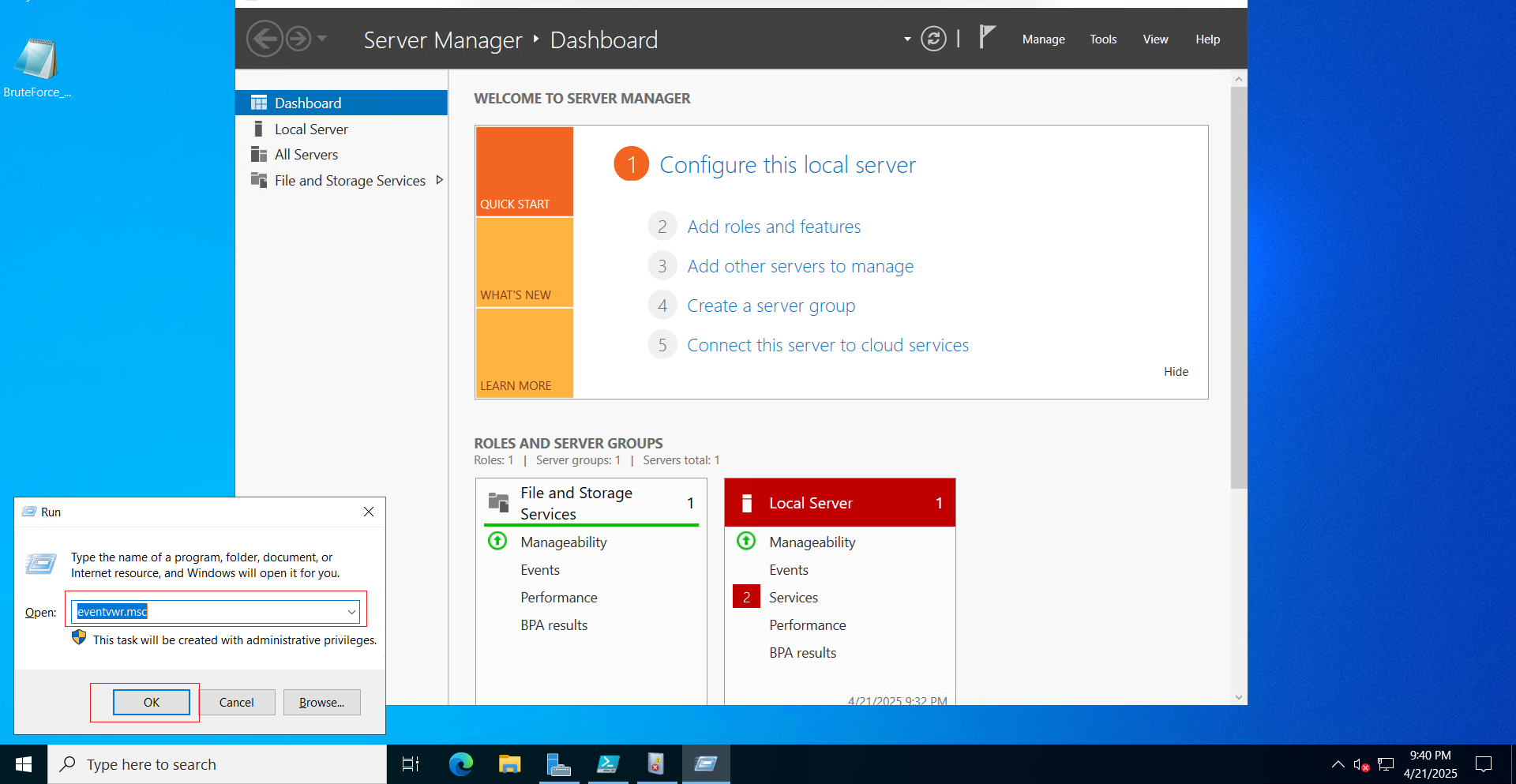
Step 1: Open Event Viewer
Step 1: Open Event Viewer
- Press 🪟 Win + R to open the Run dialog box.
- Type eventvwr.msc and press Enter.
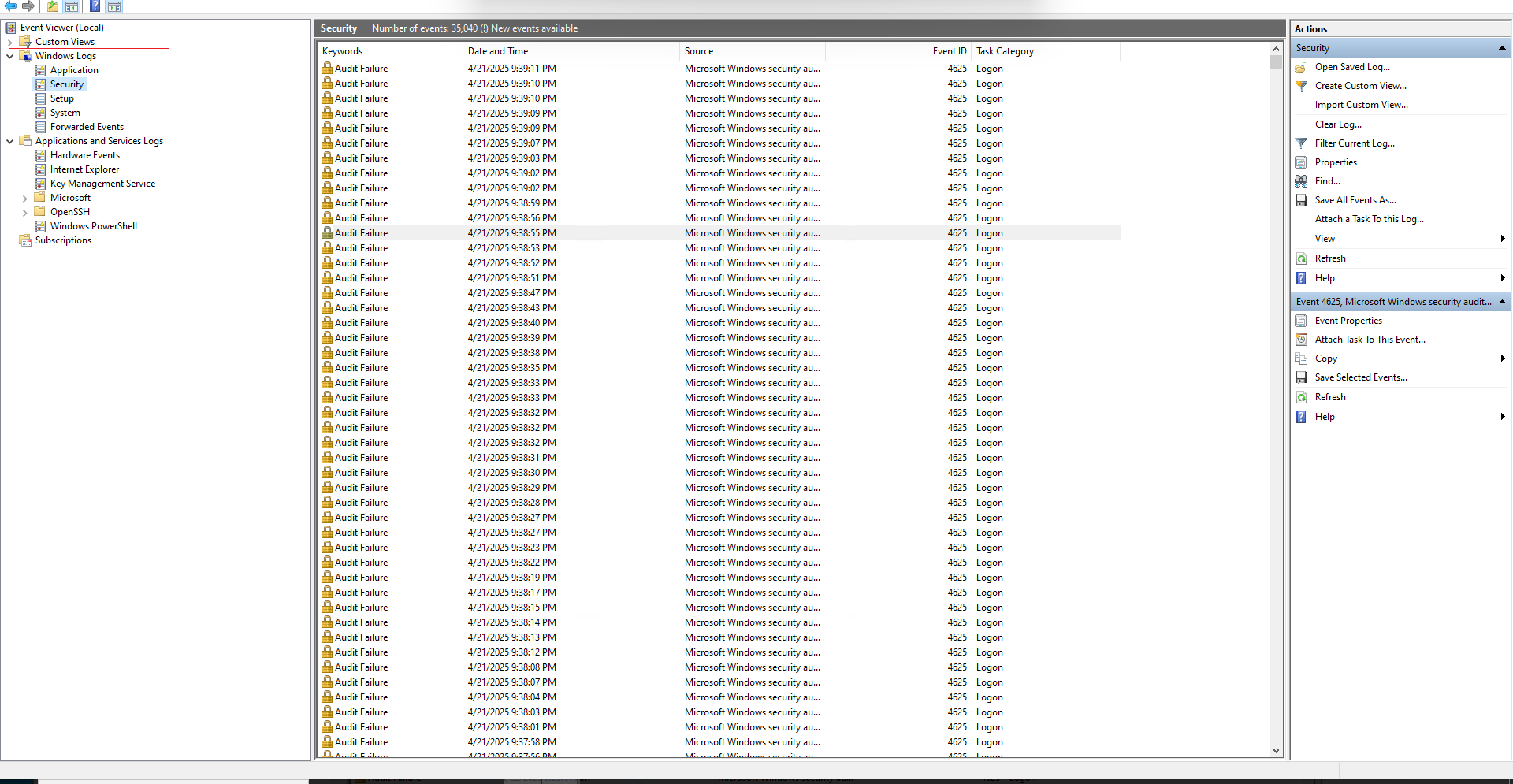
Step 2: Navigate to Security Logs
Step 3: Filter for Failed RDP Logins
- In the right-hand Actions pane, click Filter Current Log.
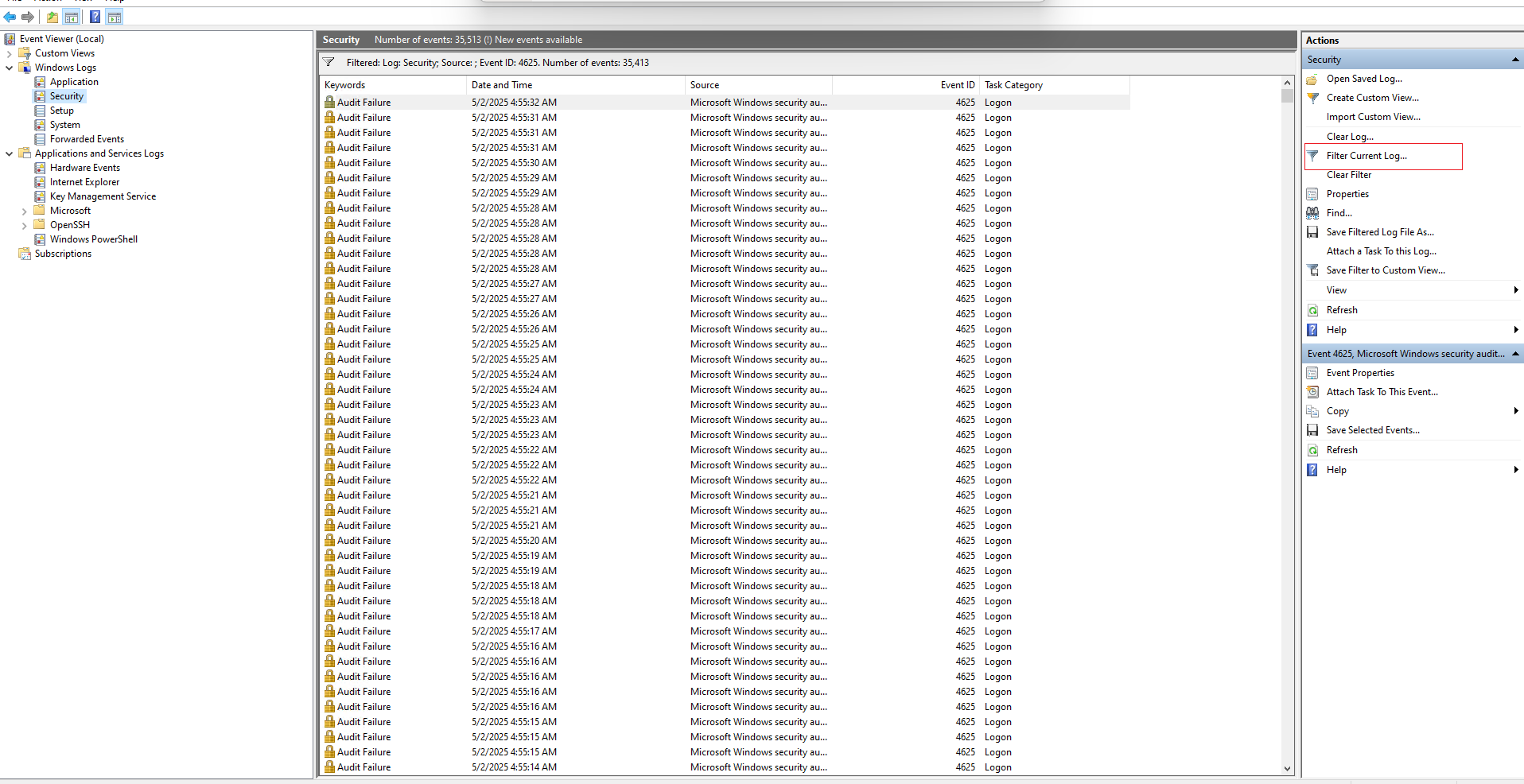
- Enter 4625 in the Event ID field to show failed login attempts.
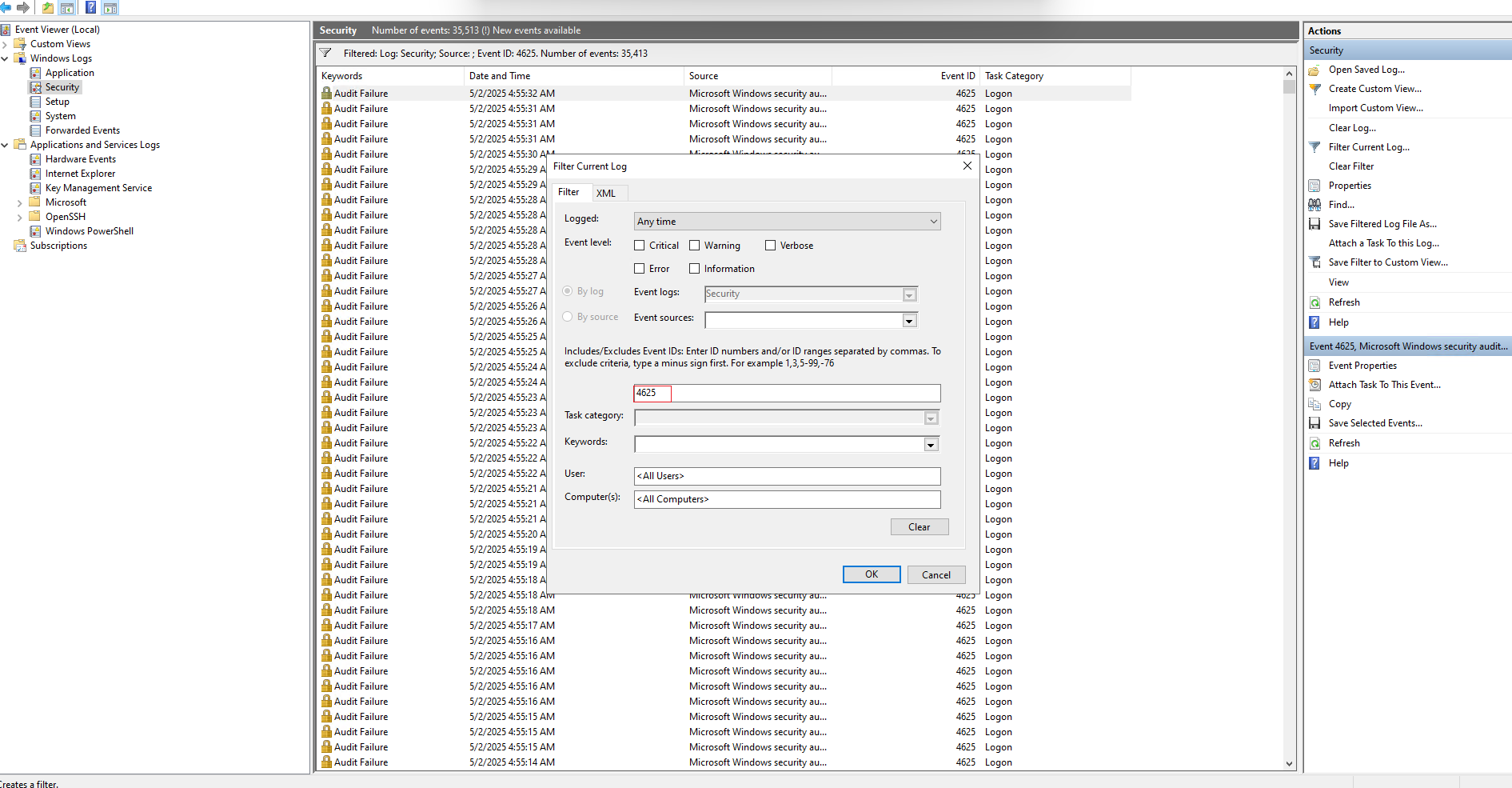
- Click OK.
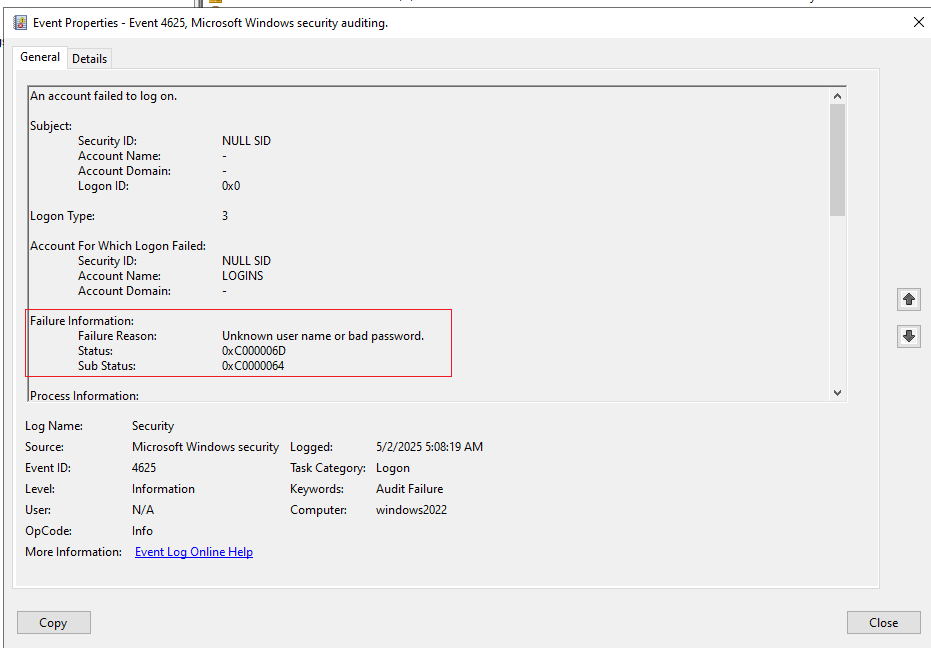
Step 4: Interpret the Log Details
- Double-click an Event ID 4625 entry.
- Review these key fields:
Conclusion
By following the steps above, you can effectively track and investigate failed RDP login attempts on your Windows Server. Regular monitoring helps enhance security and detect potential unauthorized access.
For further assistance, please contact our support team at support@ipserverone.com.