Search Our Database
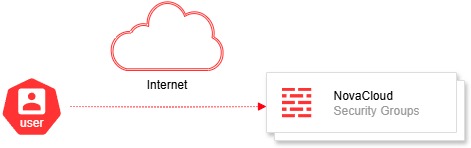
Restrict Access to NovaCloud using Security Group
Introduction
This guide explains how to secure access to your Novacloud instance by configuring security groups with restricting access to only trusted IPs.
Prerequisites
- Access to customer portal
What is Trusted IP?
A trusted IP refers to an IP (IP address or CIDR block) that has been explicitly identified as safe, permitted and authorized to access a resource.
Trusted IP configurations are relevant in scenarios, such as:
- Restricting administrative access to corporate infrastructure (e.g., SSH, RDP)
- Controlling access to APIs or web applications backend
- Enforcing compliance policies that require network-level restrictions
What is Security Group?
Security group is a set of rules attached to NovaCloud instance that defines:
- Inbound rules
- Outbound rules
Each rule based on :
- Protocol (e.g., TCP, UDP)
- Port range (e.g., 22 for SSH, 443 for HTTPS)
- Source IP or CIDR block (the trusted IPs)
If an IP address is not explicitly allowed in a security group rule, traffic from that IP is denied by default.
Best Practices
- 0.0.0.0/0 allows access from any IP address on the internet, it’s acceptable for public web traffic (e.g., ports 80 and 443)
- Avoid opening access to 0.0.0.0/0, it should never be used for administrative ports like:
- SSH (22)
- RDP (3389)
- Database ports (e.g., 5432 for PostgreSQL)
- Use Private IP Ranges for Internal Services such as databases or internal APIs, limit access to private subnets only (e.g., 10.0.0.0/16).
- Use narrow CIDR blocks (/32) for single IPs, when possible
- Review and Audit Regularly – whether unused rules can be removed, update trusted IP lists
- Pair with other security measures such as MFA, VPNs and role-based authentication for added security.
Step-by-Step Guide
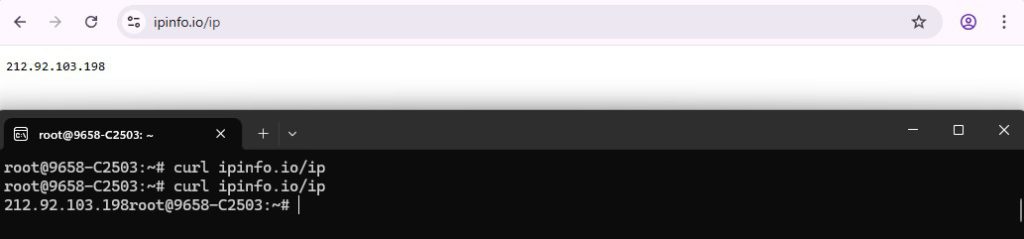
1. Identify your Public IP Address
Browser: Visit https://ipinfo.io/ip
Terminal: curl https://ipinfo.io/ip
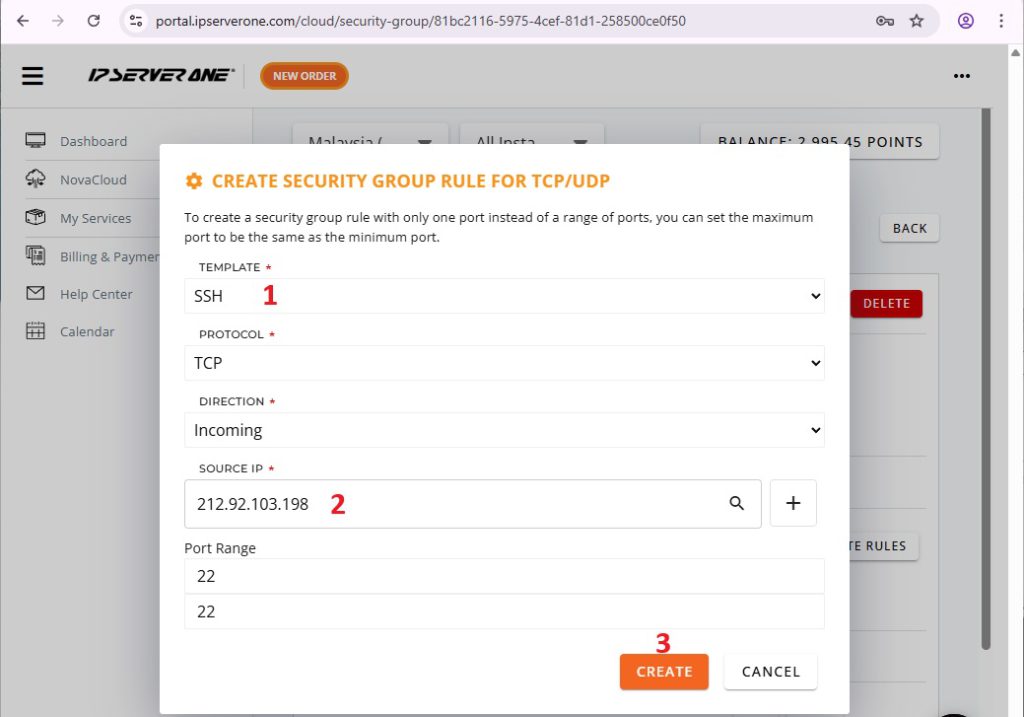
In this example, my Public IP Address is 212.92.103.198
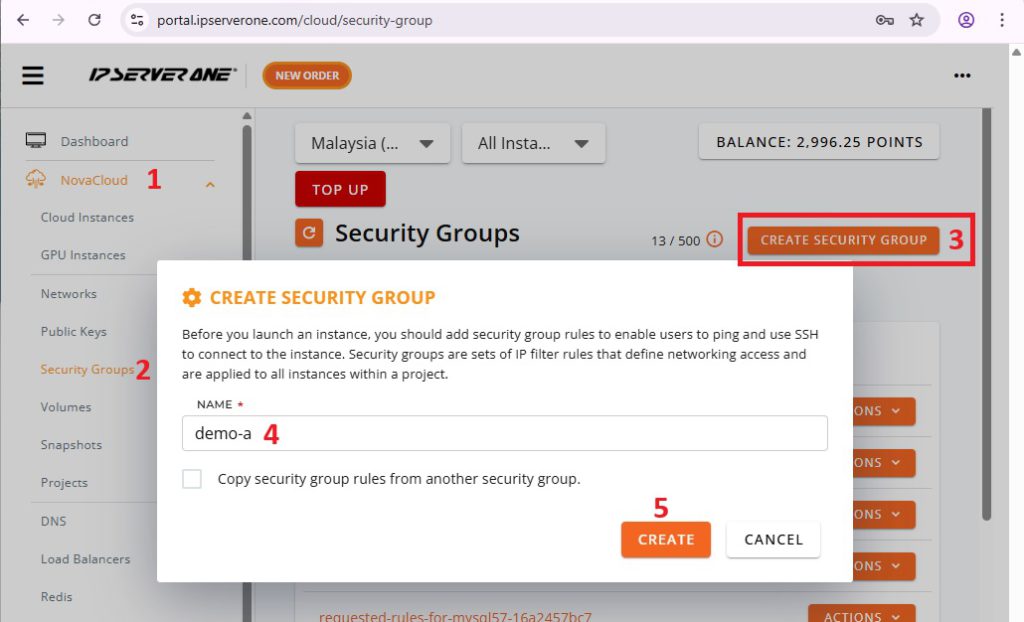
2. Create New Security Group
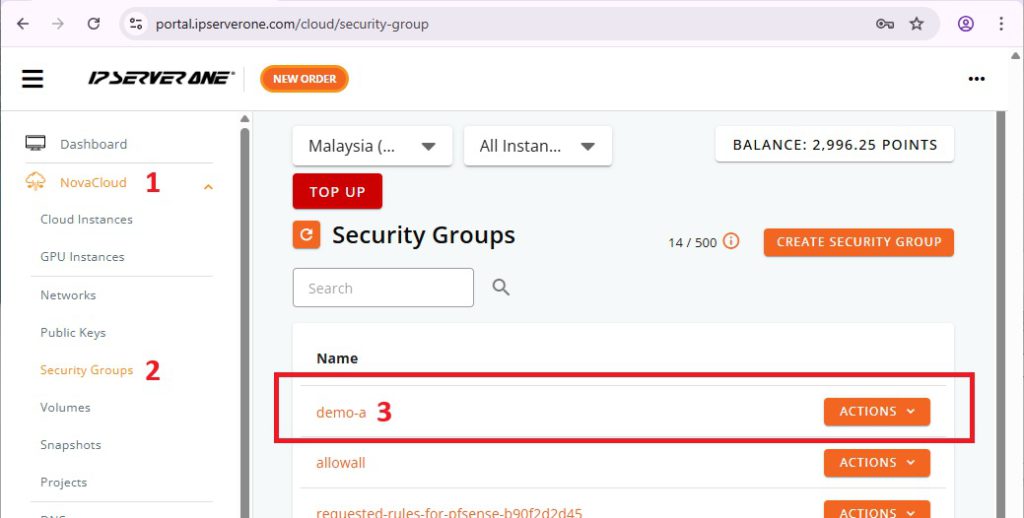
- Navigate to NovaCloud > Security Groups from the drop-down menu on the left panel.
- Click on Create Security Group
- Enter the Name of the security group
- Click on Create.
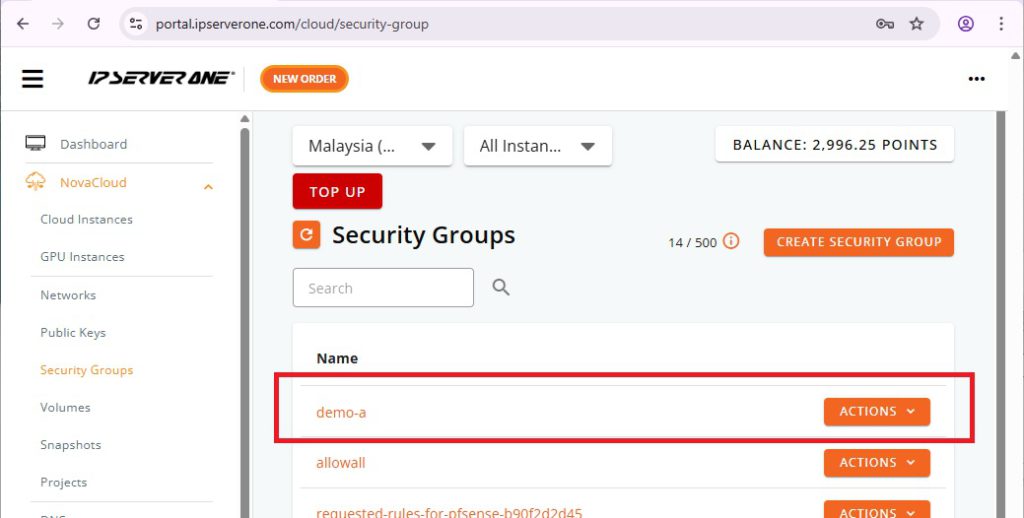
You will see that the newly created security group
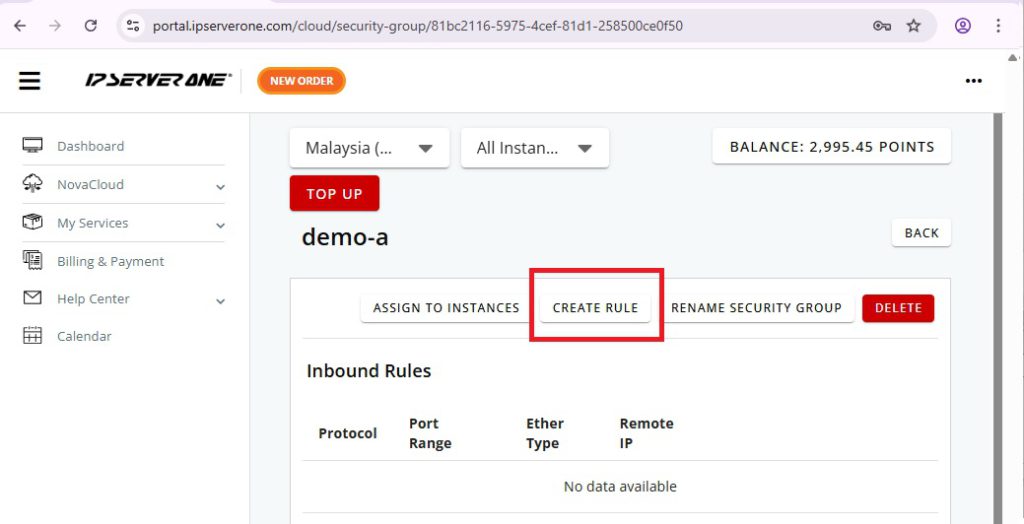
3. Navigate to Security Group Settings
- Log in to your NovaCloud dashboard
- Go to Project > Network > Security Groups
- Select the security group attached to your VM instance
Click Create Rule
4. Add Inbound Rules to Allow Trusted IPs Only
For common ports, such as SSH, HTTPS, it’s available under Template. Enter all other information as required, click on create.
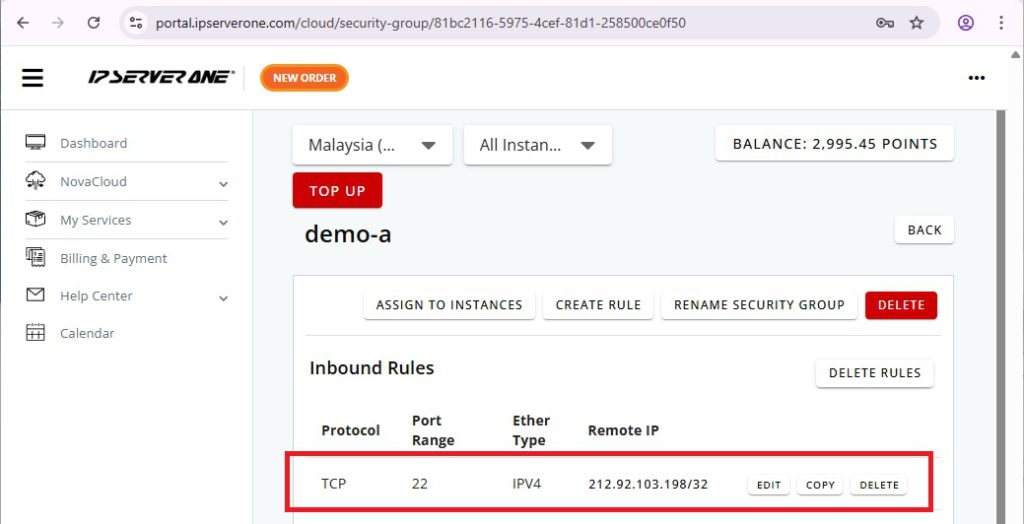
You will see the newly created inbound rule
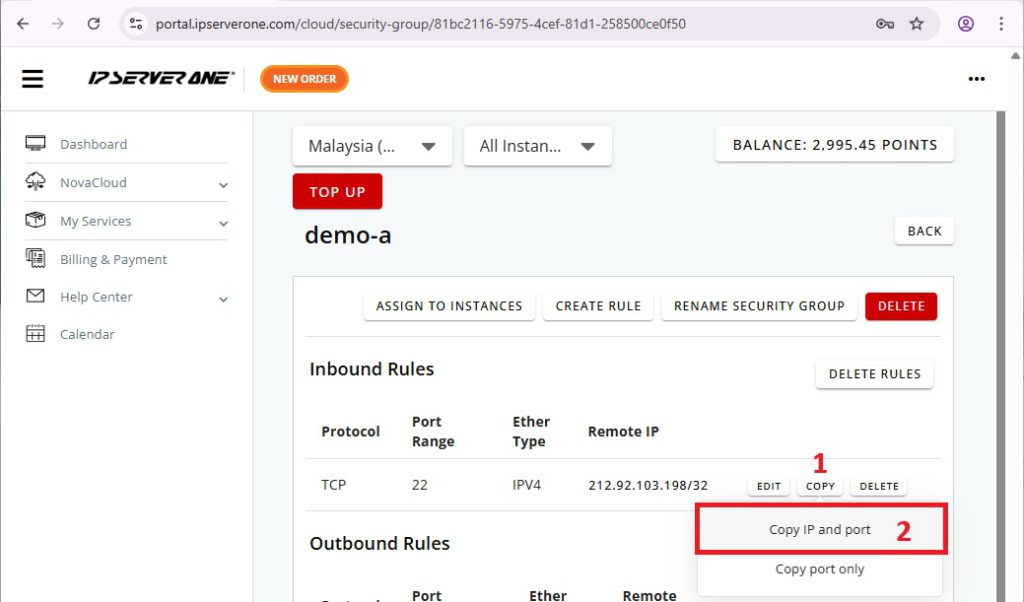
For example, now I want to allow Port 3000 (OpenWebUI) to access with trusted IP
Click Copy > Copy IP and Port
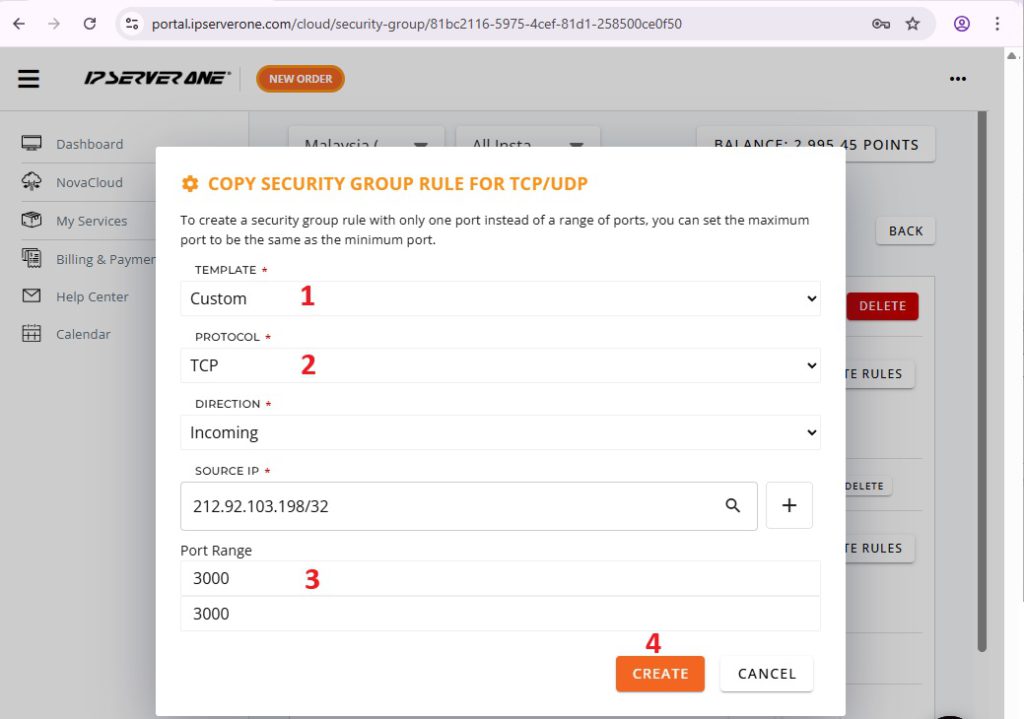
Custom Template > TCP > Port 3000 > Create
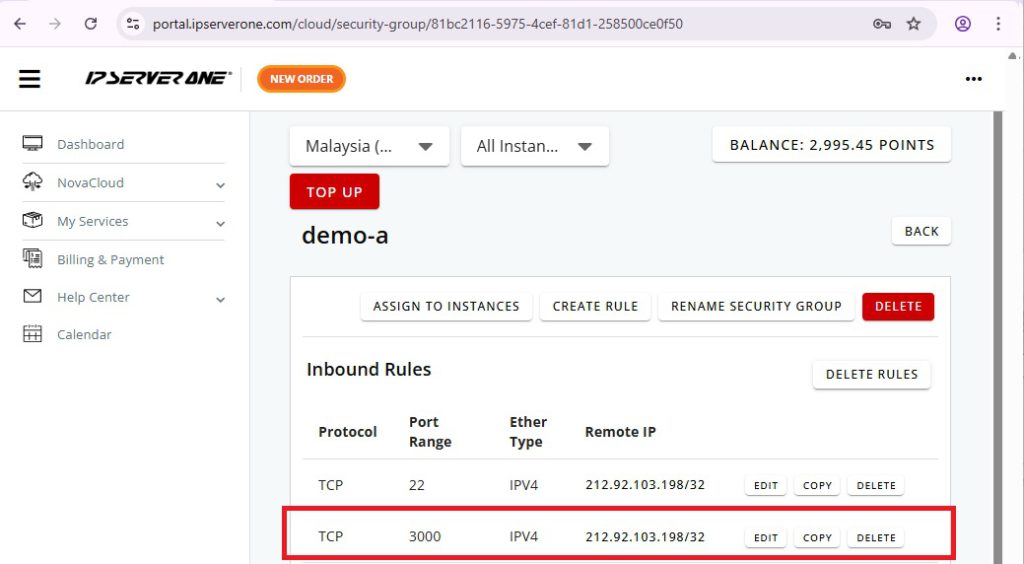
You will see the newly created inbound rule with custom port 3000
Repeat for each port you need.
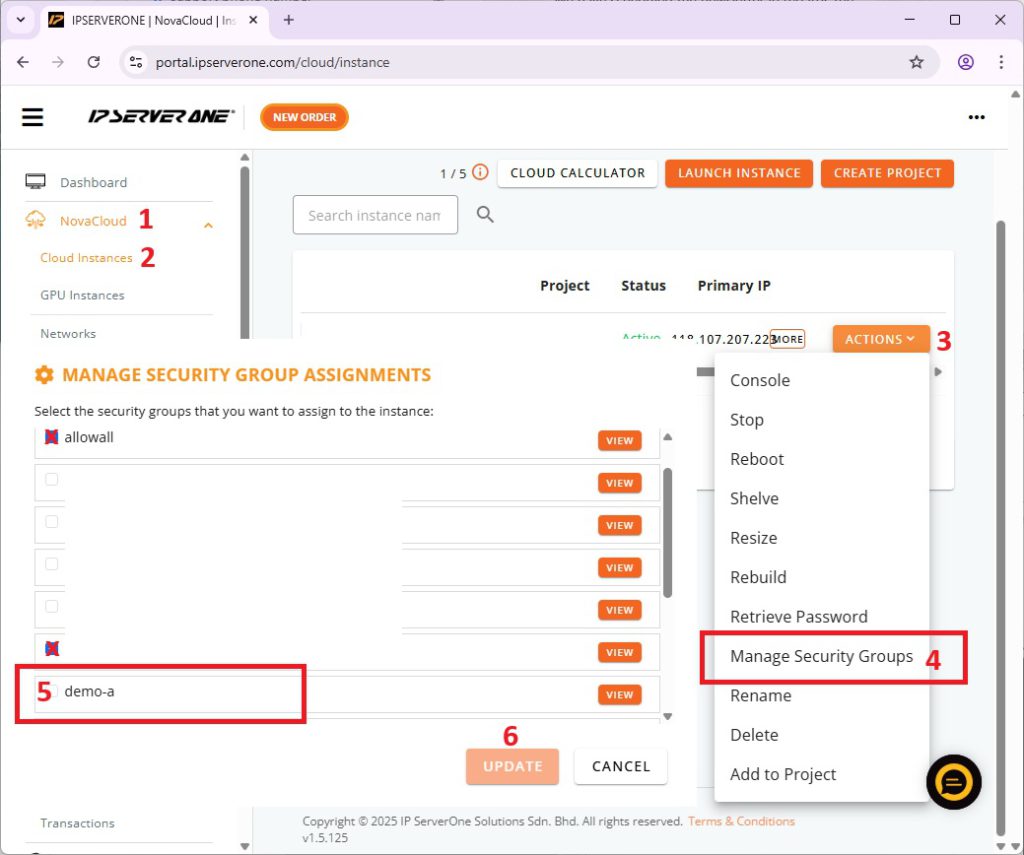
5. Assign this security group to your instance
Go to Cloud or GPU Instances, identify the instance and click on Actions > Manage Security Groups
Un-select the existing security groups, and select the new security group that you have created just now, click update
Now, this security group has been assigned to the Instance that you have chosen.
Final Verification
- Attempt to SSH to the server or open the web interface from your IP – access should work
- Try from another network such as using mobile data – access should be denied
Impact / Considerations
- Risk of Lockout: If the rule is misconfigured or your IP changes unexpectedly, you may lose access.
- Dynamic IP Users: If your IP changes often (like with home internet, dynamic IP), consider using VPN to maintain consistent access with fixed egress IP.
- Security: Open necessary ports only and setup the security group securely
Conclusion
By implementing IP-based restrictions in your instance security group, you strengthen your deployment against unauthorized access while maintaining operational control.
Need Help?
Reach out to our support team at support@ipserverone.com for assistance.