Search Our Database
How to force user password expiry in Linux server
Introduction
Password expiration is a fundamental component of account security on Linux systems. It ensures that users periodically update their credentials, thereby reducing the risk of unauthorized access due to compromised or weak passwords. By default, many Linux distributions allow system administrators to define password aging policies, including setting expiration intervals, warning users of upcoming expirations, and even forcing immediate password changes upon next login.
This article is intended for system administrators and security professionals managing user access on Linux systems, particularly in environments where regulatory compliance or stringent security protocols require periodic password changes. Enforcing password expiration can be crucial in organizational settings where users may reuse credentials across systems or where shared accounts are employed for various automated processes.
The expiration policy is controlled through utilities like chage and passwd, and the account-specific settings are stored in the /etc/shadow file. When enforced properly, password aging helps prompt users to maintain secure, frequently updated credentials. However, challenges may arise in synchronizing policy changes across multiple accounts or ensuring that forced changes do not disrupt automated tasks or login flows.
This guide provides a step-by-step walkthrough to configure or force password expiration for user accounts. It covers both regular expiration intervals and how to make a password expire immediately, ensuring the user must reset it at the next login.
Prerequisites
- A Linux system (Ubuntu 20.04+, CentOS 7+, Debian 10+, or similar)
- Root or sudo privileges
- Access to the terminal
Step-by-step Guide
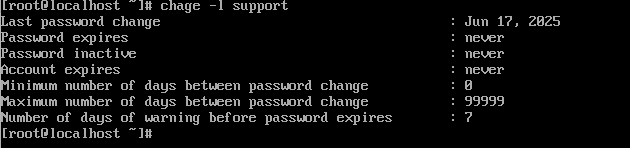
Step 1: Check Current Expiry Settings
To review the password aging policy for a specific user, run:
sudo chage -l username
This displays the current policy, including expiration, minimum/maximum age, and last change date.
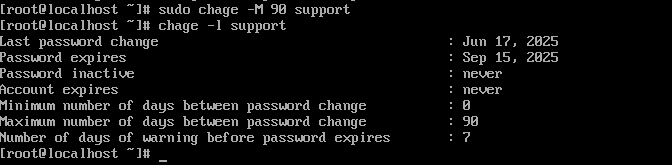
Step 2: Set an Expiry Interval
To define a maximum password age (e.g., 90 days), use:
sudo chage -M 90 username
This will require the user to change their password every 90 days.
Step 3: Force Immediate Password Expiration
To force a user to change their password at next login, use:
sudo chage -d 0 username
This sets the last password change date to the Unix epoch (January 1, 1970), effectively expiring the password immediately.
Step 4: Set Warning and Inactivity Periods (Optional)
To add a 7-day warning before password expiry and a 14-day inactivity lockout:
sudo chage -W 7 -I 14 username
-
-W 7: Warn the user 7 days before expiry
-
-I 14: Disable the account 14 days after the password expires
Conclusion
Enforcing password expiration in Linux is essential for maintaining a secure authentication environment. This guide outlines how to configure standard aging policies and how to immediately expire passwords to enforce reset at the next login. Regular updates to credentials are a cornerstone of secure system administration and should be managed in accordance with organizational policies.
Should you have any inquiries about the guidelines, please feel free to open a ticket through your portal account or contact us at support@ipserverone.com. We’ll be happy to assist you further.