Search Our Database
How to set password expiry to never for user in Linux server
Introduction
Linux systems use a password aging policy to enhance security by requiring users to change their passwords periodically. This policy can be enforced using tools like chage, which controls account aging information. However, there are scenarios where setting the password to never expire is necessary, such as for system or service accounts that require uninterrupted access or when complying with specific organizational policies.
Password aging is managed on a per-user basis and is stored in the /etc/shadow file. By default, many Linux distributions enforce a password expiration policy to mitigate the risk of compromised credentials. However, in certain administrative or production environments, it is vital to bypass this policy to ensure continuous operation and automation.
This guide is intended for system administrators, DevOps professionals, and anyone managing Linux servers who needs to prevent password expiry for specific accounts. It applies to most major distributions, including Ubuntu, CentOS, Debian, RHEL, and their derivatives. The process involves using command-line utilities like chage and passwd to update user account settings effectively.
Common challenges include understanding the implications of modifying password policies, ensuring compliance with security standards, and applying these changes consistently across systems. This guide provides step-by-step instructions to permanently disable password expiration for any user account, ensuring clarity and reducing the likelihood of error.
Prerequisites
- A Linux system (Ubuntu 20.04+, CentOS 7+, Debian 10+, or similar)
- Root or sudo privileges
- Access to the terminal
Step-by-step Guide
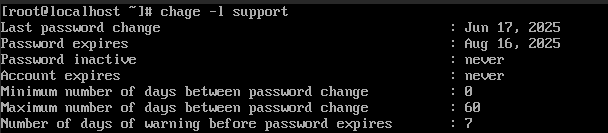
Step 1: Check the Current Password Expiry Settings
To view the current password aging policy for a specific user, use the chage command:
sudo chage -l username
Replace username with the actual user. This will display information such as last password change, password expiry date, and minimum/maximum age.
Step 2: Set the Password to Never Expire
To disable password expiration, run the following command:
sudo chage -I -1 -m 0 -M 99999 -E -1 username
Explanation of the options:
-
-I -1: Disable inactive days
-
-m 0: Minimum number of days between password changes
-
-M 99999: Maximum number of days the password is valid
-
-E -1: Never expire the account
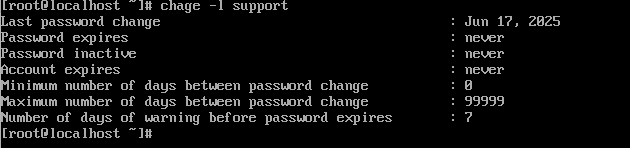
Step 3: Verify the Changes
After applying the changes, confirm them with:
sudo chage -l username
Ensure the “Password expires” and “Account expires” fields say “never”.
Step 4: (Optional) Set Expiry Policy via /etc/shadow
As an alternative method, password expiry can be managed by editing /etc/shadow directly. This method is not recommended unless necessary.
Open the file using a text editor:
sudo nano /etc/shadow
Find the line for the user and ensure the fields related to expiry (fields 5, 6, and 7) are set appropriately (usually empty or set to -1 for no expiry).
Conclusion
Setting a Linux user account’s password to never expire is a straightforward task using the chage command. This is particularly useful for service or automation accounts that require persistent credentials. It is essential to understand the implications of bypassing security defaults and ensure such changes are applied only where appropriate.
For enhanced security, it is recommended to complement this with other security measures such as SSH key authentication or multi-factor authentication when applicable.
Should you have any inquiries about the guidelines, please feel free to open a ticket through your portal account or contact us at support@ipserverone.com. We’ll be happy to assist you further.